
Cybersecurity: Protecting Your Digital World
Aug 18, 2023
Are you interested in how to create a robust cybersecurity strategy? Do you want to explore the latest cybersecurity threats and trends? Is your digital business in need of essential best practices to fortify security?
We have the privilege to listen to an executive and guru of Security Programs to understand the fundamental highlights of cybersecurity in order to create a safer online environment. The following content will summarize his ideas, interpretations and suggestions to create a safer digital world.
Creating a robust and impactful Cybersecurity Program
Being part of an organization that embraces a digital component drives us to consider an efficient cybersecurity program. The expert suggests to Focus on Business Relevance and advises to focus on Business Relevant Risk. Some questions are triggers to analyze the situation and have a better start:
- What keeps you and your stakeholders awake at night?
- What are your requirements?
- Who is responsible for risk?
Following the answers to the last question, and in order to understand what to do for risks when talking about digital safety, some highlights should be a must.
- Inquire the root causes and be prepared to remediate them strategically.
- Mitigate risks using compensating controls.
- Accept the situation to continue the next steps and know the possible consequences.
- Transfer the Insurance to a 3rd Party if needed.
- And do not Ignore the risks' factors.
Checking the requirements will lead to a stronger strategy: understand your organization, the regulatory demands, contractual obligations and corporate culture. The cybersecurity expert affirmed that “you can’t protect what you aren’t aware of” and the solution is to comprehend the environment, the critical assets and scoops, and the issues that comprise the technology stacks and perimeter.
Starting to establish a security programme requires attaching it to a model or framework that guides the plan and helps to build a roadmap. The security guru gave us the CMMI Maturity Model as an excellent example and share the steps:
0: Incomplete 1: Initial 2: Managed 3: Defined 4: Quantitatively Managed 5: Optimizing
Cybersecurity technology trends and topics
Moving forward, the expert defines some cybersecurity technology trends and topics that everyone should be aware of.
Next Gen Cybersecurity Technology Explosion:
- Simpler, easier, more modular and quicker.
- Drive Shift left
- Observability, impact and value
AI is changing both the capabilities of malicious actors and providing benefits for cyber professionals and technology
- Understanding complexities of risk
- More rapid and advanced automation for social engineering
Zero trust: the embodiment of “least privilege”, start with no access or privileges, only add what is needed when it is needed
Behavioral Heuristics: to identify anomalies and malicious activity focus on how people use technology vs. how you expect them to use it
Shift-Left: security teams have finite resources and should collaborate with their partners to manage their own risk and resolutions
National Cyber Requirements in US and Europe are and becoming more rigorous.
Cyber insurance is more challenging to get.
Why Cybersecurity Matters Headlines: Risks and Threats
Exposure to digital danger seems to be everywhere. Including the sources and variants of risks are plenty.
-
The Human Factor: People, phishing and smishing: for example, an attacker that compromised a Cisco employee’s Google account accessing private credentials. (Source - Third party trust)
-
Third Party/SaaS authorizations and integrations: for example, an attack originated with a security vulnerability in MOVEit’s software. A mass file transfer tool leaving hackers the opportunity to get sensitive data. (Source - Electric.ai)
-
Backdoor and Supply Chain Attack: for example, SolarWinds refers to the use of the method “supply chain attack”, that hackers used to insert malicious code into a system, take advantage of a third party with access to an organization's systems rather than trying to hack the networks directly. (Source - Tech target)
-
Legacy tech debt: for example, Barracuda Networks struggled to combat a sprawling malware threat which appears to have undermined its email security appliances in such a fundamental way that they can no longer be safely updated with software fixes. (Source - Krebson security).
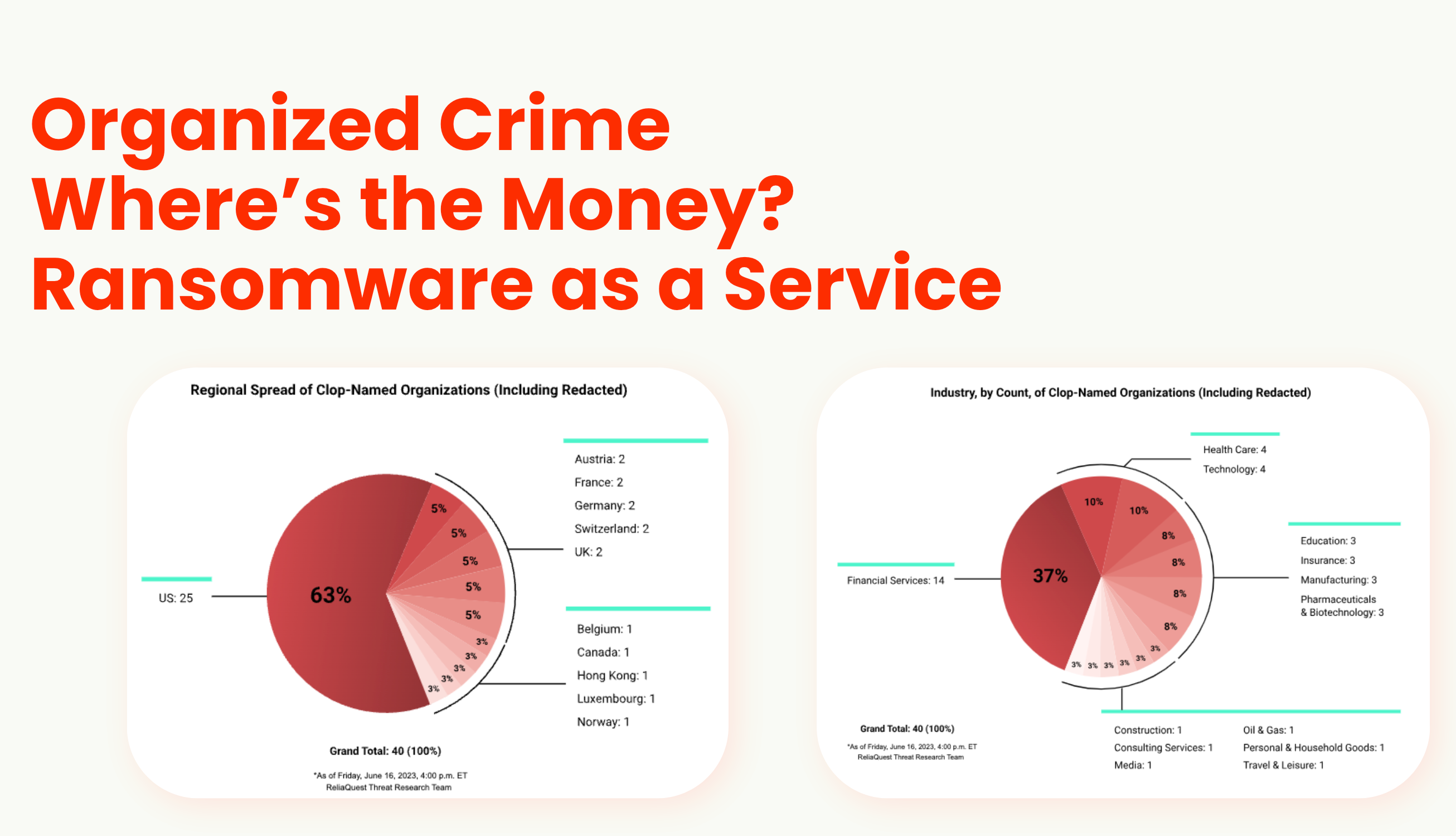
And others such as software vulnerabilities, organized crime, ransomware as a service, and identities (human and non-human).

Some essential best practices to fortify your digital defenses
The guru shares some approaches to the correct definition of cybersecurity as a vast and broad area of responsibility where **risks, management, security, data, threads, frameworks, development, integration, identity, cloud, application, metrics, automate, technology, IoT and much more are combined. **
Let’s read the expert’s advice to consider for better digital defenses:
Observability & Response
- Ask yourself: What is going on in your environment? What is at risk?
- Attack Surface Management - Know your environment, assets, perimeter, and users.
- Threat Detection and Response - What malicious activity are you experiencing? Are there necessary controls and are they effective? What will you do for an incident?
Security Operations - SecOps
End User Security
- Phishing training & Email Security
- Endpoint management & EDR
- Identity: Users, Access and Credentials
Partnerships with Stakeholders and Executives
- Shift-Left
- Driving Organizational Change
Creating a safer digital world is possible. Understanding the complexity and opportunities is a good starting point.


